In keeping with my #AzureNetworking series, Azure Bastion seems like a nice place to move to next!
What is Azure Bastion?
So Bastion went GA quite a few months ago now and I did have a little play with it then, but thought this would make a nice little article.
If you are an IT Pro or in some form of admin function, you will know what a ‘Jump Box’ is, and Azure Bastion in layman’s terms is an answer to this concept.
Bastion is a secure PaaS offering in Azure that you can create and configure to offer TLS connections to your servers (RDP or SSH) without the need to provision a specific server with published access via a firewall, without the need to provide a public IP directly onto your internal servers etc. All of these techniques are highly frowned up on by any security teams and quite frankly, you would NEVER do in a production environment, so using Azure Bastion offers secure access to your Azure hosted VM’s via a Browser!
Overview: https://docs.microsoft.com/en-us/azure/bastion/bastion-overview
What are the benefits of Azure Bastion?
As alluded above, Azure Bastion offers a Secure way to access your resources in Azure at the same time as keeping your Security team smiling and happy!
How do you configure Azure Bastion?
Firstly, lets set the scope. I have a Basic Virtual Machine in my Subscription called ‘VM01’ It is connected to my Jonnychipz-VNET in the ‘Servers’ Subnet, so will have a private IP of 172.16.1.0/24.
We can use a variety of ways to configure Bastion, PowerShell, CLI, Portal etc. For our purposes here, I will walk through a quick way to set up a Bastion in your subscription.
So, I’m going to view the VM in the Azure Portal and select ‘Connect’, then select ‘Bastion’.

Remember that this VM does NOT have a public IP, so is not contactable to anything outside of the Azure VNET that it is currently located.
Next we will click, ‘Use Bastion’
We are presented with a screen to configure Bastion. Now, as a prerequisite, Azure Bastion is expecting to find a Subnet named ‘AzureBastionSubnet’, so we can quickly set this up by clicking on the link ‘Manage Subnet Configuration’
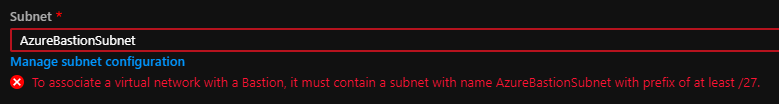
Here I have created our AzureBastionSubnet quite high in my VNET range as you will find there are many things that require specific subnets as you work through the Networking features of Azure. Azure Bastion requires a minimum of a /27 bit range, so because I have a large CIDR Block allocated I’m just going to keep this straight forward and use an entire /24 range of 172.16.200.0/24, basically so we know that anything with an address of 172.16.200.X will be something to do with Bastion!

The only other thing we need to allocate is a Public IP, so we will do this as part of the ARM template in the GUI.

Apart from maybe changing the Resource Group or hooking up to a premade Public IP object, thats pretty much it for the creation of the Bastion PaaS Service.

Click ‘Create’
After a few minutes, our Bastion has been provisioned and we can connect to our VM.

Enter the Username and Password of your VM and click ‘Connect’
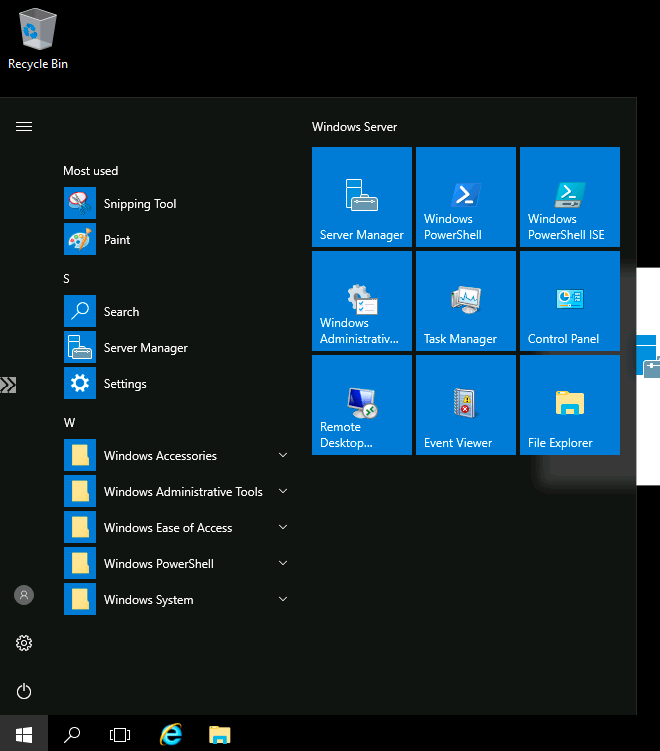
And there we have it, we are connected via the Bowser/Bastion to our VM!
We can browse to our Bastion in the Azure Portal and see our active session.

To recap. Azure Bastion is a connectivity platform for your Virtual Machines in your Azure VNET.
A Bastion is deployed in your required VNET
An admin can connect to the Azure Portal and then choose to connect via Bastion to a VM with a click over either SSH or RDP.
No Public IP is required on the VM
How do you pay for Azure Bastion?
The Azure Bastion PaaS Service costs can be viewed utilising the Azure Calculator here:
https://azure.microsoft.com/en-gb/pricing/details/azure-bastion/
Azure Networking Microsoft Roadmap

